De-risk cyber recovery with Cutover's automated runbooks
Cyber recovery is unpredictable and complex due to the difficulty in determining the blast radius of attack and data affected. Once data and systems are restored, it’s critical to understand how to improve security and the ability to recover from a cyber attack in the future. Many enterprises use static documents held in repositories like Confluence or spreadsheets, word documents, PDFs and other manual formats to execute cyber recovery which expands recovery times across siloed teams.
As cyber threats constantly evolve, recovery plans need to be regularly exercised and hardened for a strong security resilience posture. While static tools may have helped you manage cyber recoveries, automated runbooks provide a faster, more efficient and reliable way.
Automated runbooks for cyber recovery
Automated runbooks outline theset of tasks and their dependencies that need to be undertaken to complete a cyber recovery. This includes both manual activities carried out by an incident commander or IT team, and triggering automated activities like executing an Ansible script to provision the hardware, application and data. In this way, runbooks bring together human expertise and knowledge with the benefits of automation.
Cutover provides a comprehensiveand holistic solution to respondto and recover from cyber incidents. Cutover’s automated and executable runbooks enable you to gain confidence in your cyber recovery. With Cutover, you’re able to manage your teams and technology recovery stack by defining, unifying and measuring all the tasks required to get your business back online after an outage or cyber incident.
Here's how Cutover helps de-risk cyber recovery
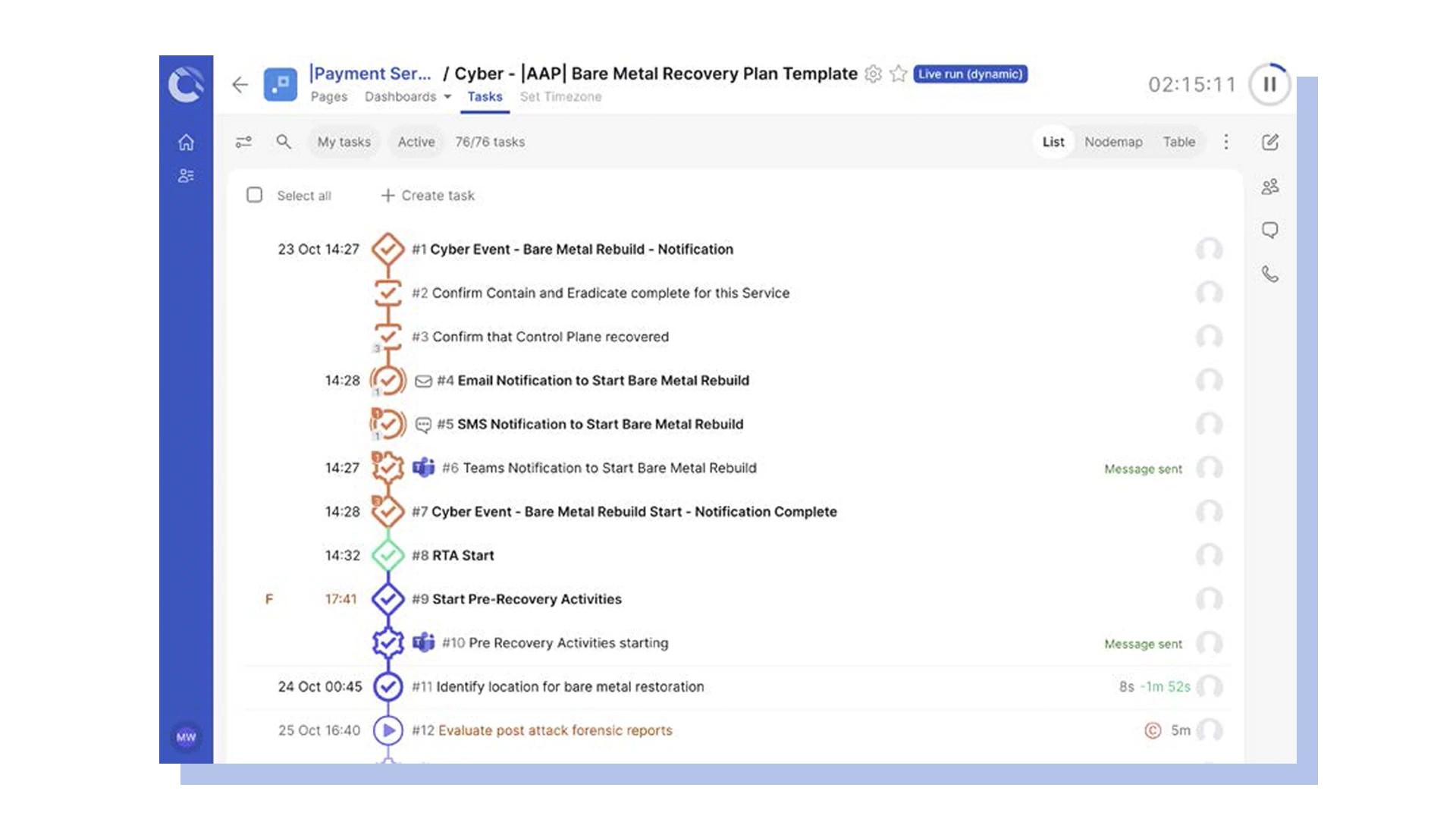
Automate orchestration for cyber recovery with runbooks
During a cyber recovery, there is a heavy reliance on individuals to manually orchestrate the teams and tasks involved. This can involve manually updating spreadsheets, spending hours on bridge calls or in war rooms, and contacting individuals by phone or email to let them know when to start their recovery tasks.
With Cutover’s automated runbooks, this manual effort is removed. The automated runbooks orchestrate this complex sequence of cyber recovery tasks, ensuring that teams and technology follow the set path in the correct order by automatically notifying people when to start their tasks and triggering automated processes. When orchestration is automated, there is no need for a person to manually sequence the tasks or spend time letting teams know when they need to take actions.
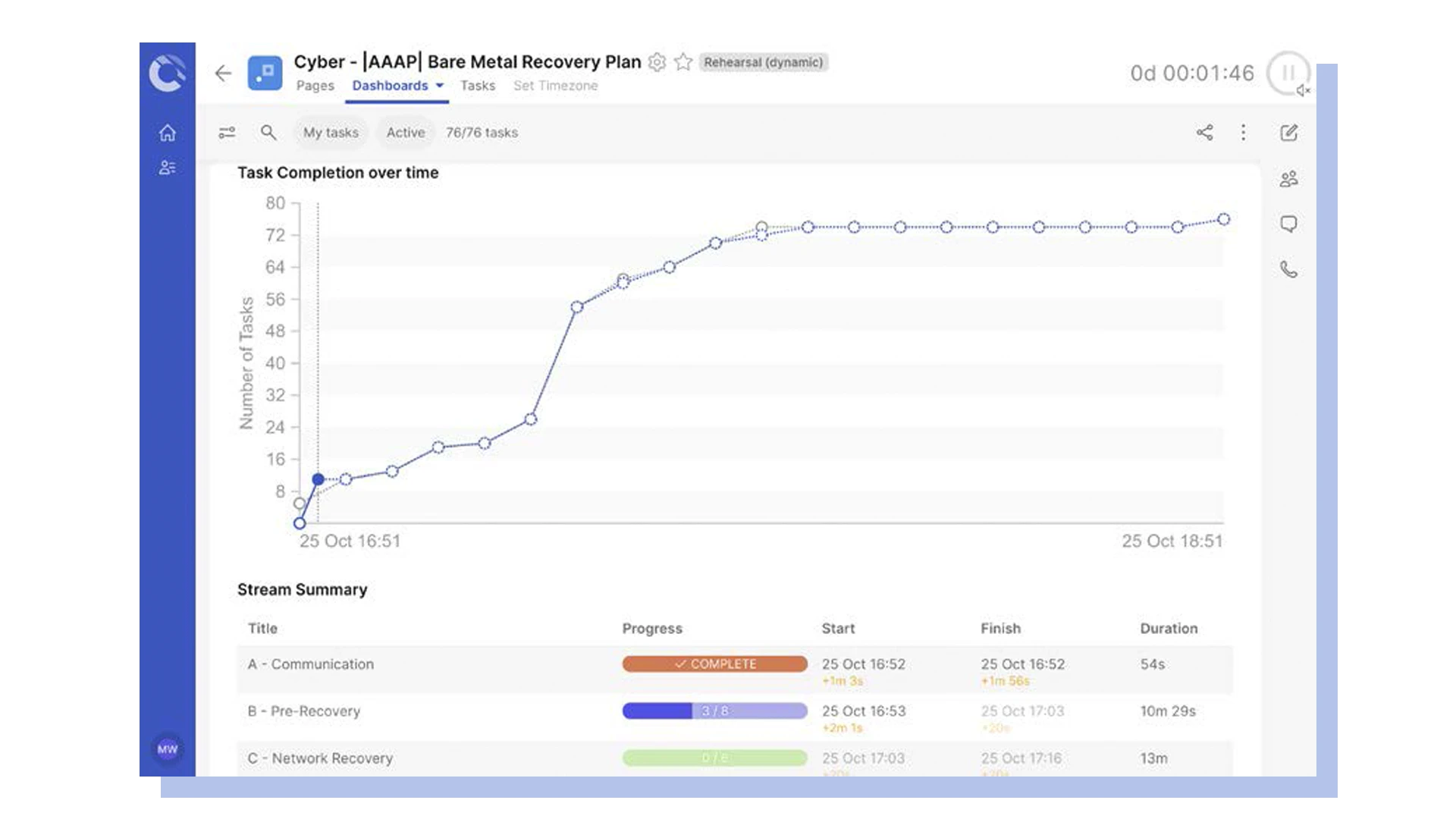
Gain enterprise visibility and report on cyber recovery progress
With automated runbooks, the progress and status of cyber recovery activities are automatically reported in real time and freely available for the chief information security officer (CISO), incident commanders and other stakeholders and teams to self-serve, so they don’t have to wait to be given progress updates. This also applies to the real time progress of multiple recovery runbooks at the same time, providing a comprehensive overview of all your in-progress recovery tasks across all applications.
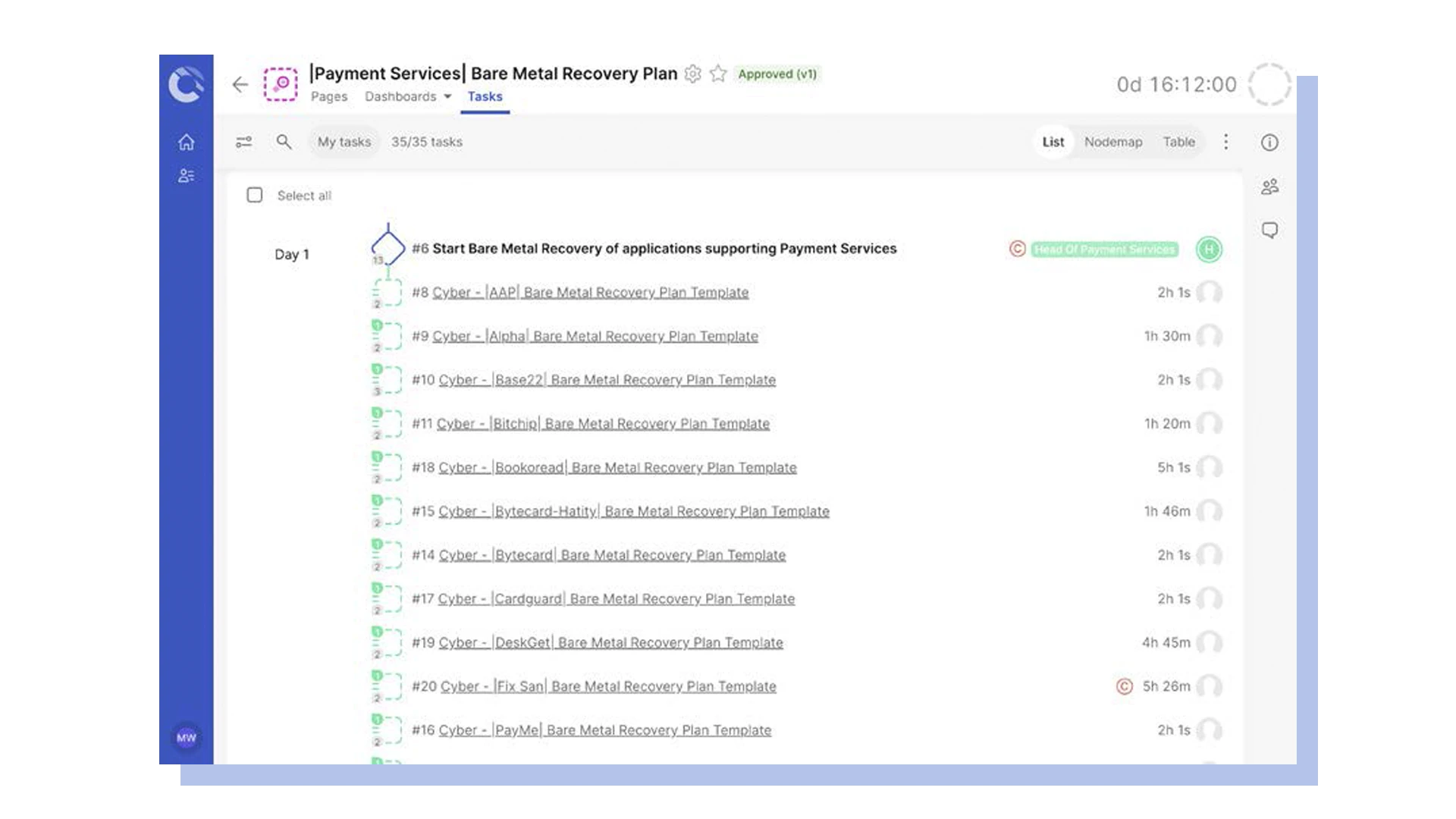
Stay agile during cyber recovery with dynamic runbooks
Automated runbooks can be dynamically adjusted during a cyber recovery by users that have the correct permissions, allowing them to adapt the plan, as needed, on the basis of new information or requirements. This is particularly useful because you may be getting new information about the blast radius or other factors after the cyber recovery has begun.
The runbook may also contain sub-routines or snippets of tasks that can automatically repeat until a set of conditions has been reached, such as integrity checks to verify that restored data and application code is running as expected before being placed back into the production network or retrying the integrity scripts.
You can also include logic-based tasks to automatically determine the best path forward when certain conditions or variables are met. This removes the need for manual intervention and improves the overall orchestration and execution of runbook tasks.
It can also be helpful to link runbooks in a parent/child relationship. For example, a parent cyber recovery runbook could have tens or hundreds of specific bare metal recovery and data integrity runbooks for each individual application or service feeding into it.
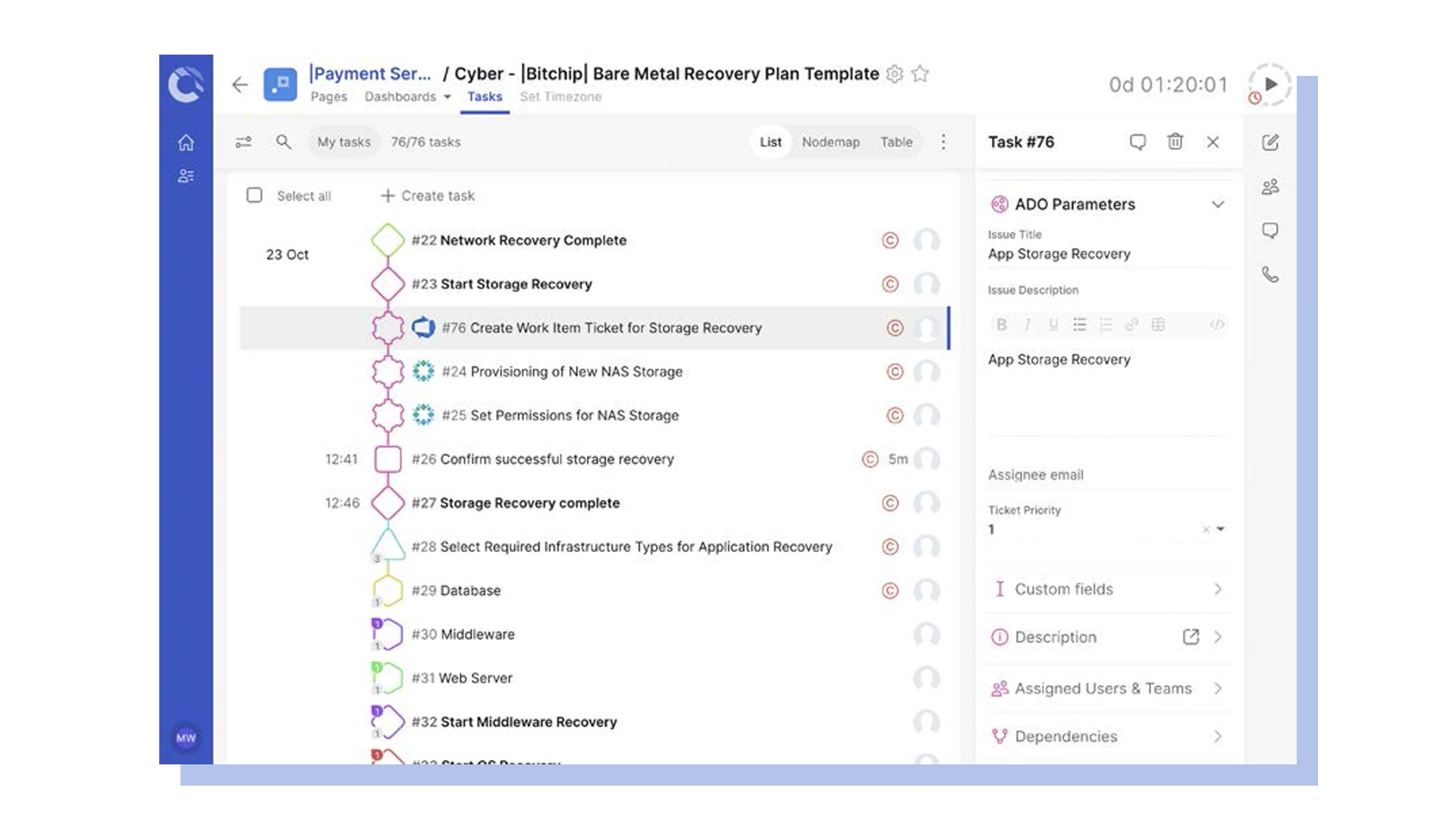
Automate runbooks with the API and integrations
Integrate Cutover’s automated runbooks with third-party platforms to create a single source of execution. This increases flexibility and productivity and reduces the risk of human error. Likewise, an automated runbook will have a well-defined API that allows you to create or query runbooks, tasks, or teams directly from third-party platforms.
During a bare metal recovery, you can automate the provisioning process or launch a task to restore data from a data vault and other recovery actions, saving time and reducing the risk of human errors. Integrations enhance the platform’s capabilities and allow for a more comprehensive recovery approach.
For example, during a cyber recovery integrate Cutover with applications including:
- ITSM and CMDB platforms
- Communications platforms like Microsoft Teams, Slack, etc.
- Infrastructure as code (IaC) tools like Ansible or Jenkins
- Security orchestration, automation and response (SOAR) platforms
- Isolated recovery environments (IRE)
- Immutable data vaults (IDV)
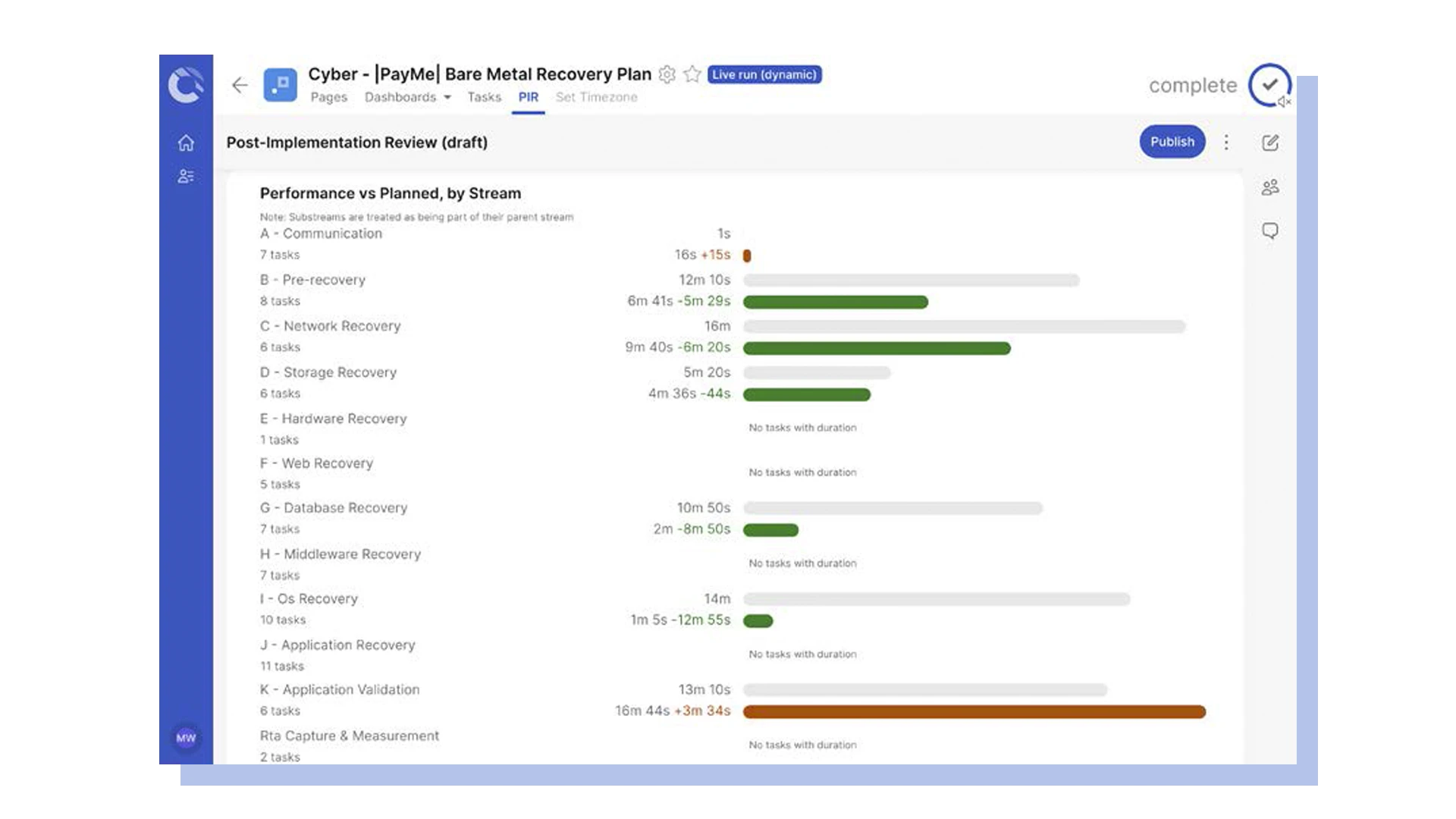
Analyze post-execution analytics and regulatory audit logs
Regulators and cyber insurers worldwide are increasing requirements on enterprises and third-party providers to prove they can recover from a cyber attack. Here are nine disaster recovery regulations financial services enterprises need to comply with. Cutover’s platform includes an auto-generated, detailed audit trail of the entire recovery process, including the time spent on each task. The immutable audit logs reduce compliance reporting time by up to 60% and helps you meet cyber regulatory and insurance requirements by making reporting to the regulator simple.
When your recovery is finished it’s essential to analyze its successes and failures so you can continue to improve your recovery process and overall execution times. Cutover’s analytics reporting automatically records the details of every action taken so you can clearly pinpoint delays or issues and how the plan can be improved.
Gain confidence in your cyber recovery processes with Cutover runbooks
Cutover provides a single platform to recover from outages and cyber incidents such as ransomware by bringing together all automated and manual tasks via dynamic automated runbooks and real-time dashboards. It enables our customers to modernize their cyber recovery strategies and restore applications and data faster. Cutover has helped the largest global financial institutions witht heir cyber and IT disaster recovery strategies.
Gain confidence in your cyber recovery and reduce your recovery planning and testing time by up to 70% with Cutover.
See Cutover's automated runbooks for cyber recovery in this short video.





.webp)

